Quantum Computers
A quantum computer, unlike a classical computer based on the Von Neumann architecture, operates in a fundamentally different manner. It leverages quantum physics to process data and store information. In a quantum computer, information is stored as a Quantum Bit (qubit). Unlike a classical bit, which can exist only in one of two states (0 or 1), a qubit is a two-state quantum-mechanical system, meaning it can exist in both states simultaneously.
One challenge in quantum computing is decoherence error, which occurs when physical qubits suffer from interferences that affect the data. To address this, logical qubits were developed. Logical qubits are constructed by arranging multiple physical qubits in a specific way to mitigate the effects of decoherence.
Below is a graph that shows a prediction made by Gartner, Inc.
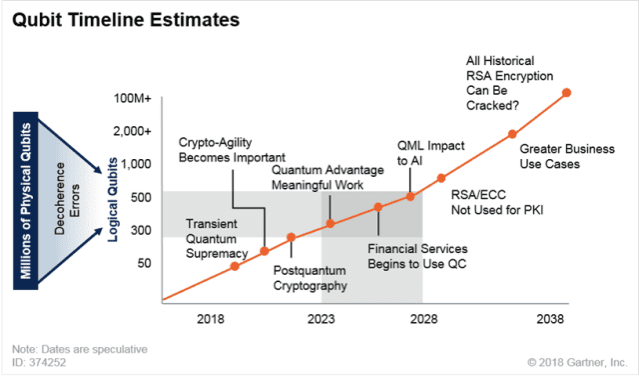
IBM is currently leading the world in quantum computing. The research made by IBM has significantly improved the field of quantum computing. Currently, the IBM Condor Quantum processor has 1,121 qubits (https://www.ibm.com/quantum/summit-2023). IBM has reached its goal of breaking the 1000 Qubits milestone (https://www.ibm.com/quantum/blog/quantum-roadmap-2033).
This shows that the advancement in quantum technologies is moving fast and we should be prepared for when such technologies will hit the market.
Quantum Technologies budgets.
The National Science and Technology Council NSTC is an organization that is established in the US and its main goal is to ensure that Science and technology that are coordinated in the policy-making process are consistent with the president’s policy priorities. One of the NSTC’s focus is on Quantum Information Science (QIS) which unifies quantum physics and information theory. QIS will have a large impact on society.
The National Quantum Initiative Act was passed in December 2018 and the US federal departments gave the green light to initiate research centers that will research QIS. On the graph below, the budget released by quantum.gov, (https://www.quantum.gov/wp-content/uploads/2023/12/NQI-Annual-Report-FY2024.pdf)
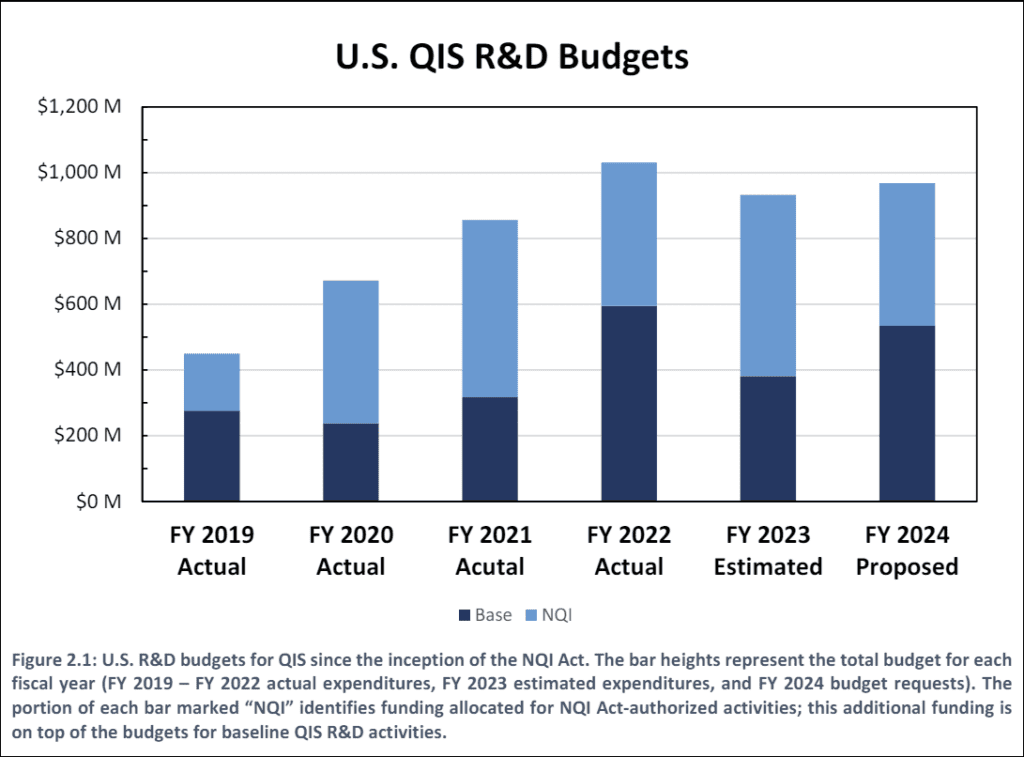
This graph shows their total budget for the QIS R&D (Quantum Information Science Research & Development). The NQI is the budget allocated by the Government and the base is their already existing budget. This shows that quantum technologies are getting mainstream.
The issues that such technology causes?
A quantum computer is extremely fast compared to a traditional Von Neumann computer. Here is an article discussing the comparison (https://www.wired.com/story/google-quantum-computing-d-wave/). In this article, it is mentioned that Google’s D-Wave Computer with 1097-Qubits solved a problem that would have taken 10,000 years to solve according to Hartmut Nevan, Director of Engineering at Google. D-Wave’s computer outperformed traditional computers by 108 times.
Shor’s algorithm is a quantum algorithm developed by Peter Shor in 1994 for finding the prime factors of an integer. Modern non-quantum-resistant cryptography relies on the difficulty of prime factorization to ensure the secure transmission of information over the internet. Consequently, a quantum computer using Shor’s algorithm could break most non-quantum-resistant cryptographic systems in seconds or minutes.
Although powerful quantum computers are not yet commercially available, it is crucial to prepare for potential security threats. One such threat is the “Store-Now-Decrypt-Later” strategy, also known as retrospective decryption. This surveillance approach involves capturing encrypted data and storing it until a sufficiently powerful quantum computer becomes available to decrypt it.
The solution to such issues
Such a problem already has a solution. Make use of Post-Quantum Resistance cryptography, PQ cryptography. These are algorithms that make use of special algorithms that are made to be hard to solve even by quantum computers. NIST, Nation Institute of Standard and Technology, made a six-year-long competition where they analyzed and reviewed many PQ algorithms and they have announced the first 4 PQ cryptography that will be used (https://www.nist.gov/news-events/news/2022/07/nist-announces-first-four-quantum-resistant-cryptographic-algorithms).
The algorithms in question are:
- For general encryption
- CRYSTALS-Kyber
- For digital signature
- CRYSTALS-Dilithium
- FALCON
- SPHINCS+
Current challenges faced to tackle such problem.
Most countries are already making their own post-quantum transition plan. Singapore is already on the move to start its transition (https://news.nus.edu.sg/national-quantum-safe-network-that-provides-robust-cybersecurity/). However, there will be challenges that will follow during this process. Below are some challenges:
- Ensuring that the new standards work seamlessly with existing hardware.
- Most System in the world still uses legacy system that may not have the computation power to support post-quantum cryptography.
- Lack of data on current systems if they can support post-quantum.
Our Framework and how can it help?
In collaboration with Cyberstorm Mauritius and the University of Mauritius, we have developed a framework to collect data on TLS servers to determine if they are correctly implemented or experiencing protocol ossification issues. Protocol ossification occurs when a middlebox, such as a firewall, is either improperly implemented or has rules that reject post-quantum connections due to their significant differences from connections using classical encryption.
Our goal is to gather data about such an issue and document it. Thus, allowing companies to have access to our data. You can read more of our research here (https://osf.io/preprints/africarxiv/kbn3d).
Currently, we are still working on the analysis. Last time we scanned Mauritius only, now we are scanning the Continent of Africa. This will require lots of time to have the final results. Our project is available on GitHub here (https://github.com/JoottunAtish/tldr_project).
Code Involvement:
- Atish Joottun (BSc Computer Science, UoM, Year 1)
- Poshan Peeroo (BSc Computer Science, UoM, Year 1)
- Kevin Yerkiah (BSc Computer Science, UoM, Year 1)
Research Paper Involvement:
- Atish Joottun (BSc Computer Science, UoM, Year 1)
- Poshan Peeroo (BSc Computer Science, UoM, Year 1)
- Kevin Yerkiah (BSc Computer Science, UoM, Year 1)
- Anwar Chutoo (Lecturer at UoM)
Conclusion.
Quantum computing is rapidly advancing, necessitating immediate action to ensure data security. The National Institute of Standards and Technology (NIST) has already selected several post-quantum cryptographic algorithms to serve as the current standard. These standards will be implemented as part of the Post-Quantum Transition Plan. At Cyberstorm, we have proactively begun transitioning to a post-quantum resistant network, starting with our operations in Mauritius.
Author
Atish Joottun (BSc Computer Science, UoM, Year 1)
